Basic understanding of NSG Logging
According to https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-nsg-manage-log
NSG Logs 2 kind of data: GroupsEvent and GroupRuleCounter
GroupEvent
The event log contains information about which NSG rules are applied to VMs, based on MAC address. The following data is logged for each event.
GroupRuleCounter
The rule counter log contains information about each rule applied to resources.
What can I monitor
Based on the previous assumptions you can monitor
- The event of an NSG rule hits by network traffic
- The number of time a single rule was applies to a resource
Note
The GroupEvent table fields can be misleading. You are not able to know which source IP is hitting the rule unless the rule contains a single source IP condition. (That’s the real meaning of the field conditions_sourceIP_s)
Things get tricky even more if you start with a set of rules that contain a single source IP with Deny Action and then switch to a rule with Deny for Any source with a single Allow rule for source IP allowed.
In this scenario you are unable to indentify IP address that will hit the rule with Deny Action.
Let’s demostrate this in practice.
I used the Application Gateway demo from Azure quick start template library to deploy a full infrastructure made up 2 webservers (with NSG) into a vNet with a Application Gateway to balance the traffic between 2 machines.
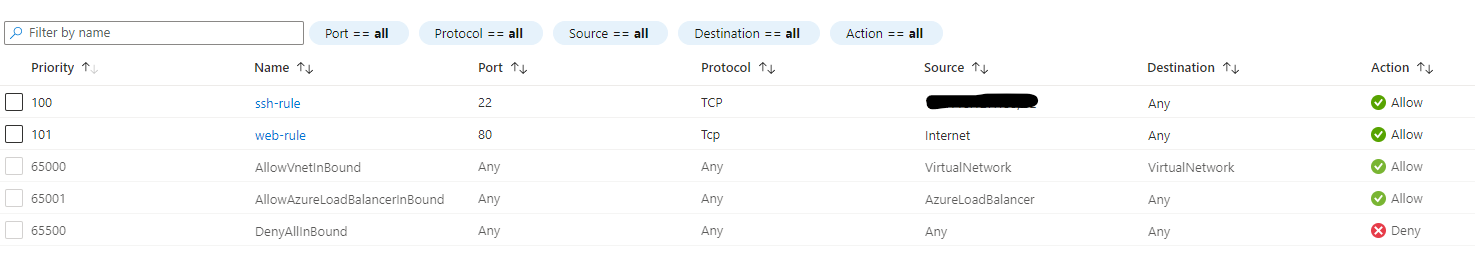
NSG had both same settings as below picture
Let’s concentrate for a while on the very first rule.
I set the Source IP to my IP and I trying to establish an SSH connection.
Everything worked fine and you get trace of the connection in the log with the below query:
AzureDiagnostics
| where ResourceProvider == "MICROSOFT.NETWORK"
| where Category == "NetworkSecurityGroupEvent"
| where direction_s == "In"
| where type_s == "allow"
| project-away systemId_g, SourceSystem, _ResourceId, TenantId, ResourceId, ResourceGroup //just to concentrate on fields value that are importantwith the below results:
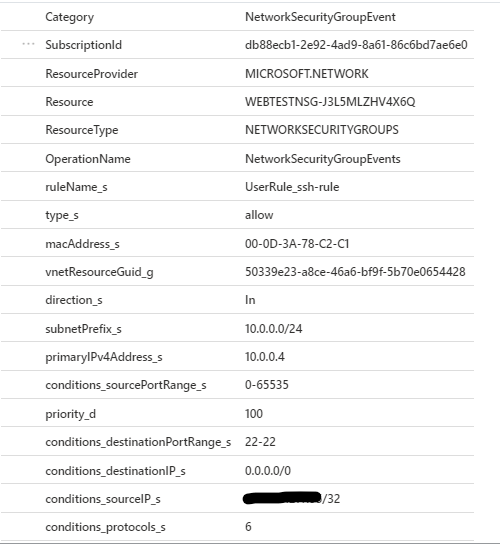
All good. What if we change the rule to disallow access from my IP?
Will be able to track who is trying to connect to SSH?
The short answer is not. Let demonstrate it:
- I changed the ssh-rule source IP to an address that is different from mine
- tried to access by ssh to the vm
the only thing I can find in is that the DefaultRule_DenyAllInboud was hit with no information about the IP tried to access.
AzureDiagnostics
| where ResourceProvider == "MICROSOFT.NETWORK"
| where Category == "NetworkSecurityGroupEvent"
| where direction_s == "In"
| where type_s == "block"
| summarize by ruleName_s
NSG simple doesn’t care about anything else but their rules.
If a rule is matched you have a record with all information (IP Address and MAC address of the NIC) where the rule was applied. But nothing about the source IP.
The bottom line is that you will be able to track explicitly denied or allowed single IP rules but to track who is trying to use something unauthorized you can’t rely on NSG Logging. You have to use something else.
(Hint NSG Flow Logs.)
The following query can help understand in a quantitative way is someone is trying to connect and isn’t successful.
AzureDiagnostics
| where ResourceProvider == "MICROSOFT.NETWORK"
| where Category == "NetworkSecurityGroupRuleCounter"
| where type_s == "block"
| summarize count() by Resource, ruleName_s, type_s, direction_s, primaryIPv4Address_s